Automation Beyond Onboarding
Dynamic monitoring
Rely on a closed-loop workflow solution where every capability directed at uncovering risk at the start of the relationship is kept on during the execution of it.
Stay ahead of the unknown
More than 8 out of 10 third party “misses” result in operational disruption according to Gartner and every 9 in 10 FCPA enforcement actions against companies involve a third party.
This is how you can stay ahead.
360° view of third-party risk

Combine risk datasets
Understanding the risk levels posed by third parties within each risk category is important but insufficient. Gathering an aggregate picture of the overall level of risk deduced from the combination of all risk categories such as ABAC, ESG, privacy, cyber and other risks, will provide you with a clearer view of how risky it is to enter a given relationship. With the integrity Platform’s Third Party Risk Management solution, you can create a centralized, composite view of all risks related to a given third party which will allow you to more accurately assess the risk of engagement and well as more astutely monitor the impact of potential changes on the overall third party risk level.
Connect external and internal risk and monitor emerging overlap
In many cases, an organization’s third party population is owned by different business departments, vetted through a process unique to each unit, through systems that are disconnected. Any risk identified in one system is not connected to a central third party profile leaving the aggregate view of risk incomplete. What happens when a third party is subject of an incident report filed by an employee through the company’s whistleblowing program? Does the relevant business unit get notified of a potential new risk that might impact the engagement? Or how can a business unit be alerted when an current or potential engagement is identified as too risky based on assessments conducted by other parts of the business?
The underlying infrastructure of the Integrity Platform enables the integration of all compliance processes that sit around your TPRM program to directly connect with every third party profile, allowing for any internal conflict, investigation, donation, gift or any other relevant data to be automatically captured and stored under the respective third party profile in real time.

Flag engagements that exceed initial scope
Beyond connecting every piece of data related to your third party, the platform further aggregates values to roll-up the sums of total engagements; these may be an aggregate value of gifts submitted by an employee that involve a given third party, donations offered, additional services or other. These types of disclosures should be connected to the third-party profile and flagged as a risk indicator that might alter the initially calculated level of risk.
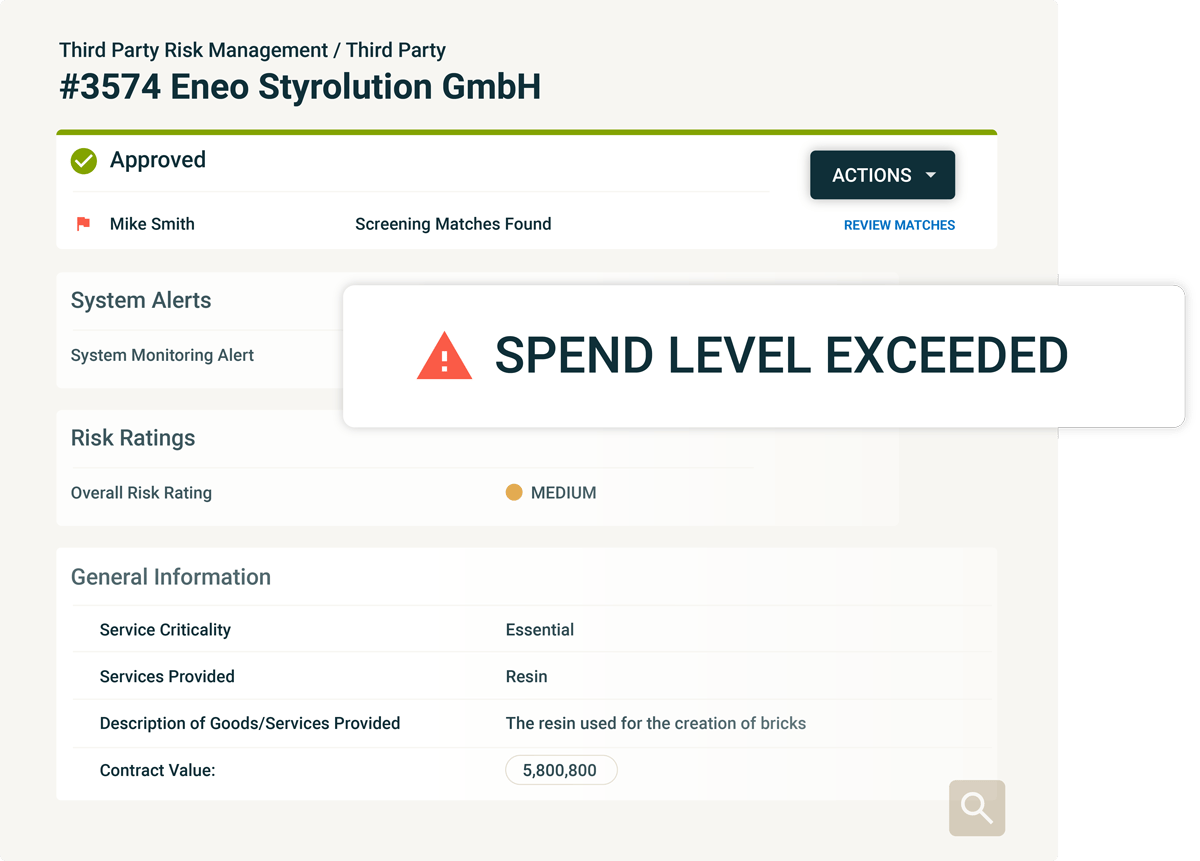
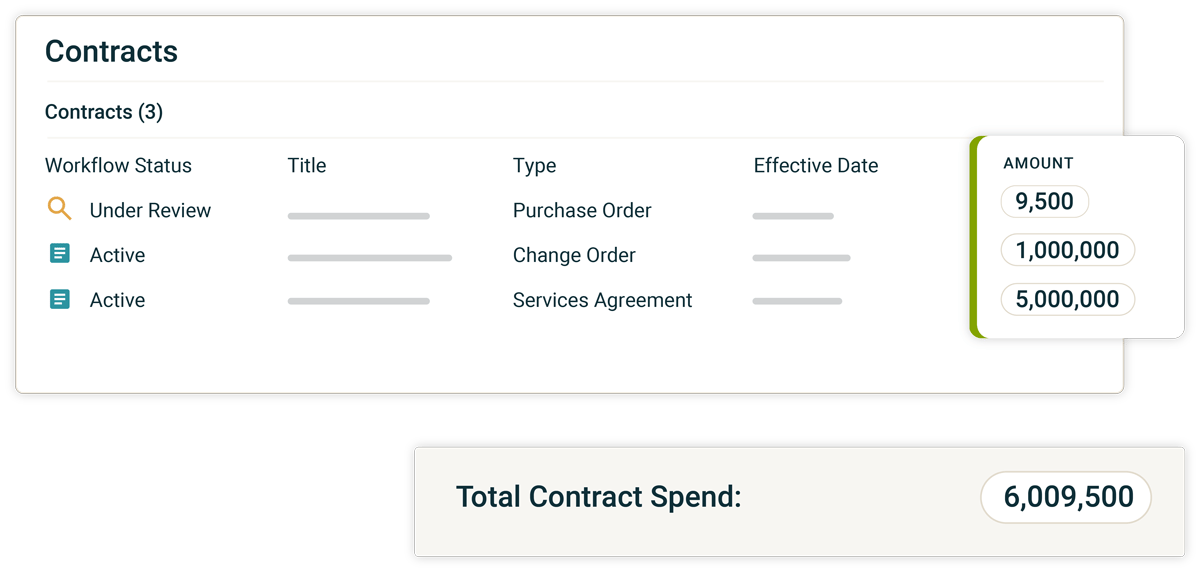
The other way around is also true. Engaging with external entities through, for instance, a donations and sponsorships program should trigger due diligence processes. The Integrity Platform allows for such connections. Employees disclosing gifts to an unknown entity can automatically trigger a screening into the newly created entity. The nature of the action triggered - screening or other - will depend on the requirements of the business, the system can therefore be configured accordingly.
Tap into event-driven revetting
Unlike periodic revetting, event-driven revetting is triggered by changes in the third party profile that offset a due diligence workflow. Event-driven revetting could be triggered by a change in contract value, a surpassed gift threshold, a new sanction entering into force, or other. Event-driven revetting is configured based on conditions, if met, trump the pre-set revetting schedule to ensure that potential risks are surfaced, assessed and mitigated as soon as they occur.
Governance and workflow automation beyond onboarding
With the Integrity Platform’s workflow automation technology you can build business rules that allow for speedier due diligence without compromising on checks and balances in the process. But third Party risk does not start and stop at the initial engagement or assessment, it is a fluid, dynamic process. Which is why every automation, advanced algortihm, risk modelling and cross-platform and application data integrations apply just as efficiently during post-onboarding allowing you to be notified of changes in the relationship that might require your attention and proactively identify risk within your third party population.
The same can be said about the program’s gatekeepers, with data access governed to reflect your organizational structure, notifications and delegation of mitigating and revetting actions are brought to the attention of the appropriate stakeholders ensuring that actions are executed on time and in the right context.


