Blog
2025 Wrapped: What Shaped Compliance This Year
Monday, December 22, 2025
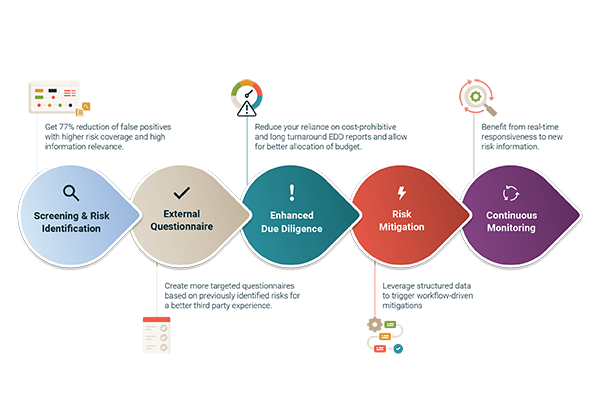
Discover the key compliance trends of 2025, from AI governance to real-time third-party risk management, and learn how to prepare for 2026.
Learn More